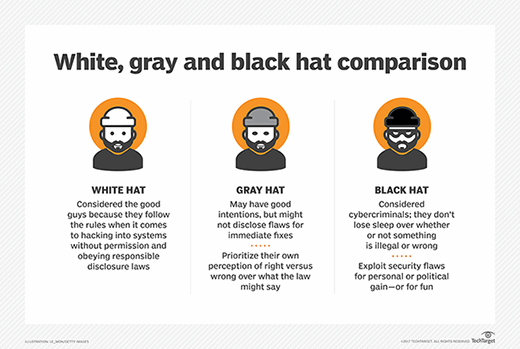
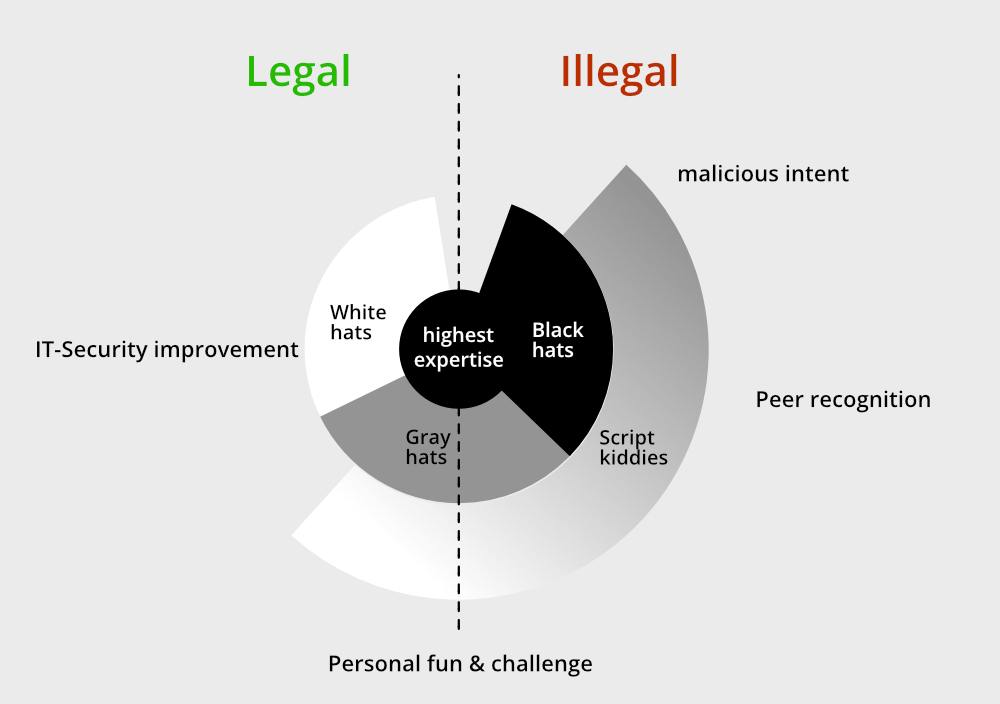
GK Computer Centre - Explained: What Are White Hat, Gray Hat, and Black Hat Hackers? Not all hackers are inherently bad. When used in mainstream media, the word, “hacker,” is usually used
Black And White Incognito Face Icons Stock Illustration - Download Image Now - Hat, Vector, Computer Hacker - iStock